| Vendors |
| Communication & other equipment. Easy to choose, easy to buy |
|
|
| Easy way to buy complex equipment |
 | Main Catalog Catalog Secure communication Secure communication External Scrambler External Scrambler |  |
External scrambler connecting to any phones via Bluetooth
Bluetooth Scrambler
|
Main specifications
|
|||||||||||||||||||||||||||
Review
The Kripti bluetooth encoder is part of a comprehensive information security system
Kripti bluetooth is a unique miniature encryptor that allows you to encrypt speech while negotiating a mobile phone with super-strong cryptographic algorithm, which is used by state, military and commercial organizations around the world.
Kripti provides cryptographic protection of information in the transmission of voice over the standard voice channel of GSM, UMTS or any other cellular communication.
The built-in Kripti bluetooth memory card provides storage of encrypted information on it.
Highest degree of cryptographic protection of information in Kripti
It is provided due to hardware implementation of encryption algorithms and hardware generation of encryption keys.

Benefits
Work with any mobile phone that has a Bluetooth module
Kripti bluetooth can be connected as a headset to any mobile phone or tablet equipped with a Bluetooth module. No additional software is required to run Kripti bluetooth.
Strong encryption
The speech is encrypted and decrypted into Kripti. The encrypted data is transmitted via Bluetooth to the subscriber's mobile phone and then through the GSM network of the cellular operator to another subscriber. Encryption directly in Kripti eliminates the interception of unencrypted speech and the possibility of information leakage through the fault of the cellular operator.
Kripti encryptors are immune to viruses, because they operate under their own unique operating system.
It is impossible to decrypt negotiations and transmitted data even with the loss or theft of Kripti
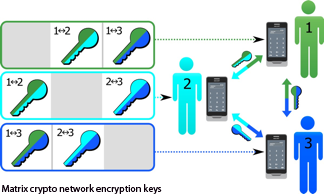
If the Kripti is stolen or lost, the attackers will not be able to access the encryption keys, because encryption keys are stored in encrypted form in Kripti.
Each Kripti subscriber has a unique set of keys for communication with each other subscriber. Therefore, the loss or theft of one Kripti does not affect the security of other subscribers in any way. The encryption keys for connections to this subscriber can be deleted by the other Kripti subscribers from their encryptors. A set of keys is generated by the Kripti network administrator using the encryption key generator and can be easily changed if necessary, and
compromised keys - removed from the encryption key database.
Principle of operation
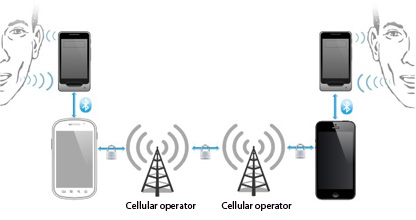
When encrypting speech in GSM mode, the transmission of encrypted speech from one subscriber to another is carried out through the GSM channel of the cellular operator. Thus, Kripti allows you to encrypt speech in a normal telephone conversation.
After connection of subscribers, depending on Kripti settings, encrypted or unencrypted conversation will begin. While there is an unencrypted conversation, the subscriber can talk either through Kripti or by mobile phone, depending on the settings of the phone. After the beginning of encryption, the conversation is possible only with the use of Kripti as a handset, because the mobile phone will hear the interlocutor's encrypted speech.
Kripti encrypts the subscriber's speech and sends it in encrypted form via Bluetooth to a mobile phone.
Encrypted speech is transmitted through the GSM network of the cellular operator to the mobile phone of the second subscriber and then via the Bluetooth channel to its encryptor where the decryption takes place.
Decrypt the speech can only the subscriber with whom the conversation is conducted, because for communication with each subscriber has its own encryption key.

Thus, speech is encrypted in Kripti of the first subscriber, decrypted by the second party's encryptor, and transmitted between two mobile phones in encrypted form. For confidential communication each subscriber needs his Kripti.
Related products
You may also be interested in the following products






 Your basket
Your basket 

































